In an era where technology intertwines deeply with our daily lives, the rise of sophisticated scams poses a significant threat to individuals and businesses alike. From phishing schemes to elaborate Ponzi schemes, the landscape of fraud continues to evolve, making it crucial for everyone to stay informed and vigilant. The…
-
-
In the ever-evolving landscape of cybersecurity threats, watering hole attacks have emerged as a sophisticated and insidious method used by cybercriminals to compromise targeted individuals or organizations. As we navigate through 2024, understanding the nuances of these attacks becomes crucial for both individuals and businesses to bolster their defenses effectively.…
-
On July 19, 2024, millions of users worldwide experienced disruptions in accessing critical Microsoft services, including Azure, Microsoft 365, and Teams. This widespread outage, attributed to [brief description of the cause, e.g., a technical issue or server outage], underscored the interconnectedness of modern digital infrastructure and the impact of such…
-
In an increasingly digital world where our identities and personal information are stored and accessed online, the security of our credentials—usernames, passwords, and other sensitive data—is paramount. Whether you’re an individual managing personal accounts or an organization safeguarding critical business systems, practicing good credential hygiene is essential to mitigate the…
-
In recent years, Multi-Factor Authentication (MFA) has become a cornerstone of cybersecurity measures, offering an additional layer of protection beyond passwords alone. However, as cyber threats evolve, so do methods to circumvent these security measures. One such method is MFA bypass, which poses significant risks to individuals and organizations alike.…
-
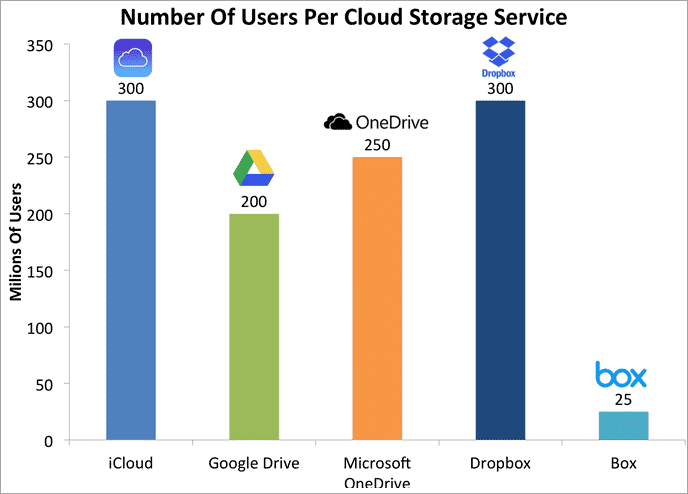
In the era of digital transformation, personal cloud storage has revolutionized the way individuals manage and access their data. From photos and documents to music and videos, the convenience of storing everything in the cloud offers unparalleled accessibility and flexibility. However, this convenience comes with inherent risks that every user…
-
Social Media Horror Show Twitter and WhatsApp were recently breached, resulting in more than 500 million users having personal data stolen. Social media attacks provide new opportunities for bad actors to target user accounts with increasingly sophisticated attacks. In this episode, starring Robert Davi as our CFO, Jack, we learn…
-
Being a part of IT Industries is quite fun and a race. Being a software developer is not easy. We always run like “Age niklo warna koi aur age nikal jayega”. They say a 9 hours job only and takes more than 10/11 hours per day, and you still think…