Introduction: Briefly introduce the Colonial Pipeline ransomware attack that occurred in May 2021. Highlight its significance as a major cyber incident affecting critical infrastructure and causing widespread disruption. 1. Overview of the Attack: Explain how the ransomware attack targeted Colonial Pipeline, a major U.S. fuel pipeline operator. Describe the initial…
-
-
Twilio hack investigation reveals second breach, as the number of affected customers rises. Cybercriminals are becoming more sophisticated in their approach, with Twilio becoming one of more than 130 organizations to fall victim to a large-scale VISHING and SMISHING campaign. The financial as well as emotional damage of such attacks…
-
Social Media Horror Show Twitter and WhatsApp were recently breached, resulting in more than 500 million users having personal data stolen. Social media attacks provide new opportunities for bad actors to target user accounts with increasingly sophisticated attacks. In this episode, starring Robert Davi as our CFO, Jack, we learn…
-
What is clone phishing? Attack of the Clones! News publisher, The Guardian, fell victim to a suspected phishing attack, through which the personal information of UK staff members was stolen. Phishing has evolved to include “clone phishing,” which is highly sophisticated and more difficult to spot. A clone phishing attack…
-
The New Realities of Vishing: Voice Phishing Hotel and casino giant MGM Resorts reported losses from a recent vishing attack that exceeded 110 million dollars. Vishing involves a convincing phone call, rather than email, to trick targets into divulging sensitive information. With robocalls, telemarketers and full-on cybercriminals all trying to…
-
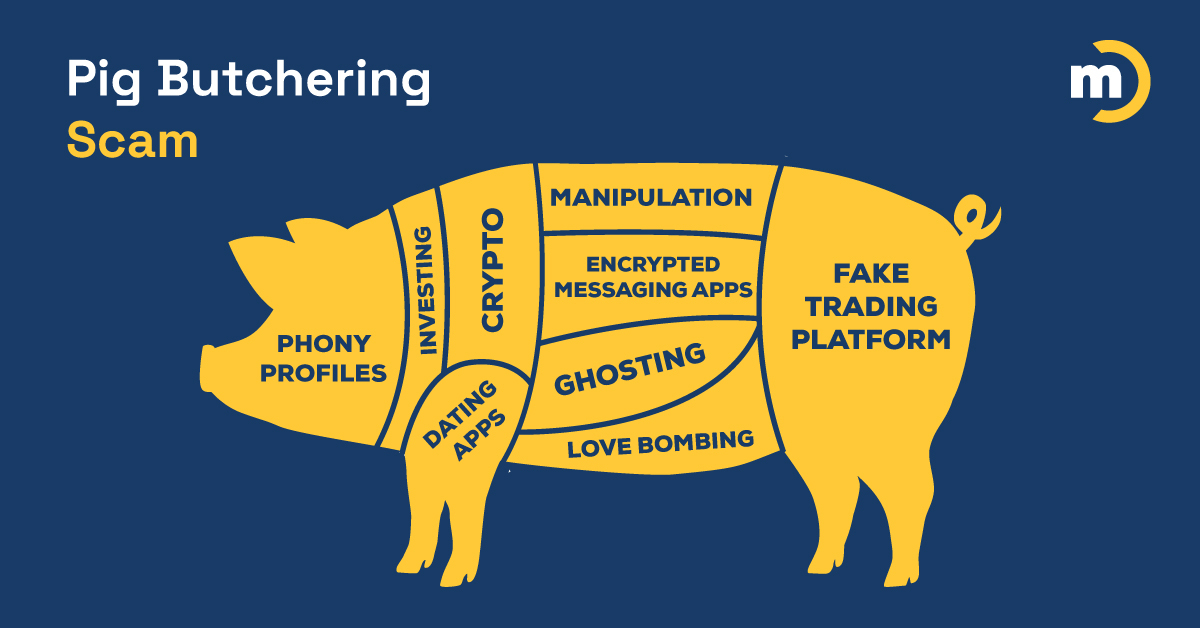
‘Pig butchering’: Former romance scammer reveals tactics. The ‘Pig Butchering Scam’ has become the scourge of the internet. A long con that tricks victims into sending money to fraudulent investment platforms, it has exploded to become the costliest scam out there, with victim losses totaling tens of billions of dollars…
-
Zero Trust Cybersecurity: ‘Never Trust, Always Verify’ Grand Theft Auto video game developer, Rockstar, and ride-share giant, Uber, both suffered recent, similar attacks that occurred within a few days of each other. Both incidents could have been avoided by employees adhering to a strict policy of – ‘verify before you…
-
Has your Facebook or Instagram or Snapchat been cloned yet? Inside the rise of social media identity theft (and what to do about it). Cases of social media identity theft have skyrocketed in recent weeks, with victims and their loved ones being scammed — so are any of us really…
-
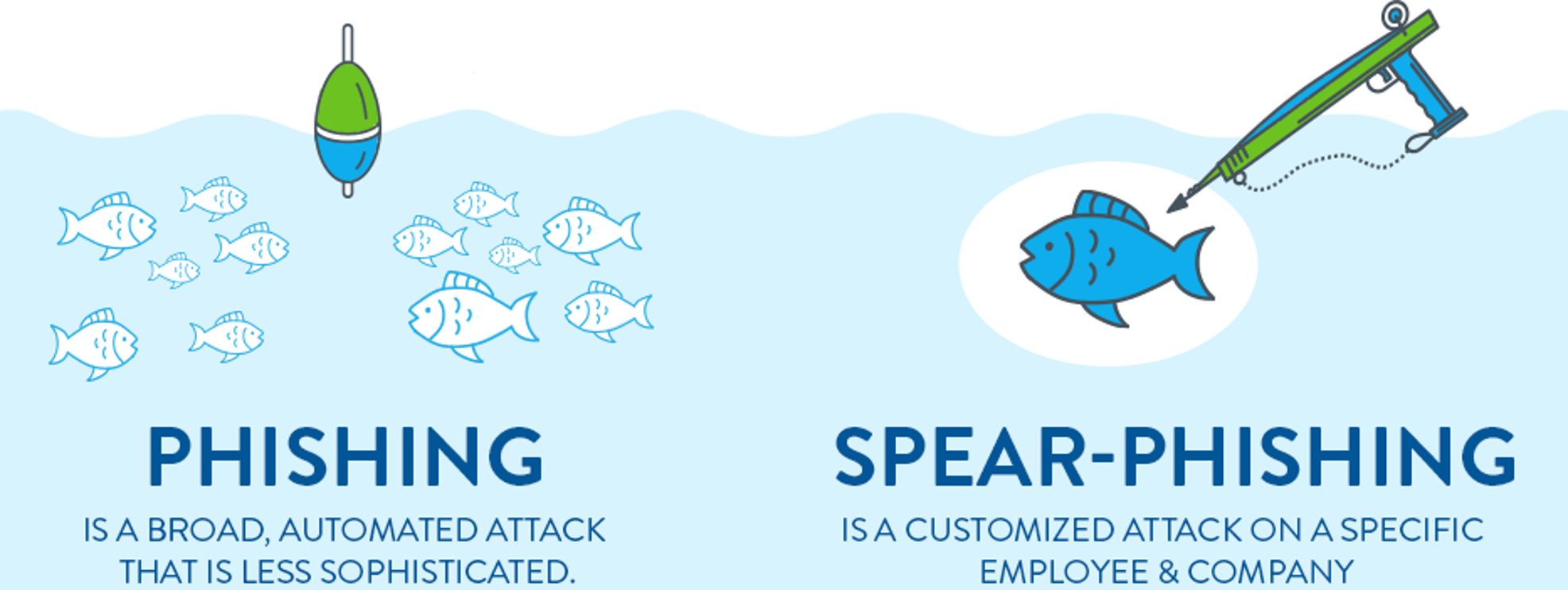
Messages and Emails are not always friendly What is Spear Phishing? Does it go to help me to get a big fish while phishing? Of course, it will help, but not you because you are going to be that fish 🐠 Let’s know how. Spear phishing is used to target…
-
“Smishing” means “SMS Phishing” Global agencies have recently warned consumers of a major spike in SMS phishing, or “smishing”, attacks. One such campaign targeted customers of the multinational shipping company UPS. In this episode, starring Andrew Lawrence as Mike, we see a firsthand account of how a smishing attack plays…