In recent years, Multi-Factor Authentication (MFA) has become a cornerstone of cybersecurity measures, offering an additional layer of protection beyond passwords alone. However, as cyber threats evolve, so do methods to circumvent these security measures. One such method is MFA bypass, which poses significant risks to individuals and organizations alike.…
-
-
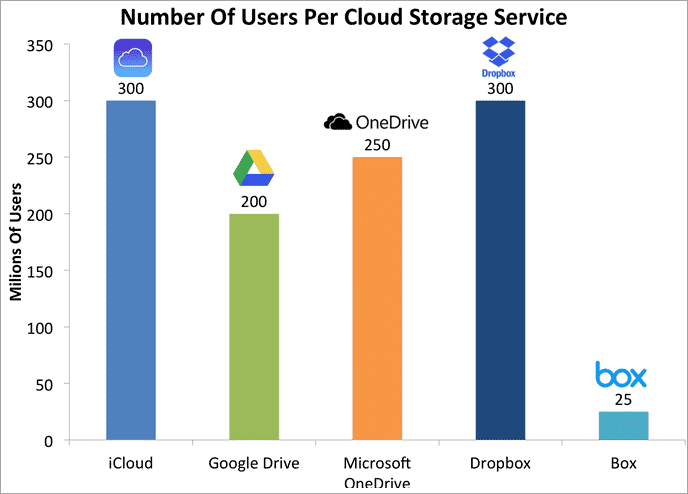
In the era of digital transformation, personal cloud storage has revolutionized the way individuals manage and access their data. From photos and documents to music and videos, the convenience of storing everything in the cloud offers unparalleled accessibility and flexibility. However, this convenience comes with inherent risks that every user…
-
Introduction: Briefly introduce the Colonial Pipeline ransomware attack that occurred in May 2021. Highlight its significance as a major cyber incident affecting critical infrastructure and causing widespread disruption. 1. Overview of the Attack: Explain how the ransomware attack targeted Colonial Pipeline, a major U.S. fuel pipeline operator. Describe the initial…
-
Twilio hack investigation reveals second breach, as the number of affected customers rises. Cybercriminals are becoming more sophisticated in their approach, with Twilio becoming one of more than 130 organizations to fall victim to a large-scale VISHING and SMISHING campaign. The financial as well as emotional damage of such attacks…
-
Social Media Horror Show Twitter and WhatsApp were recently breached, resulting in more than 500 million users having personal data stolen. Social media attacks provide new opportunities for bad actors to target user accounts with increasingly sophisticated attacks. In this episode, starring Robert Davi as our CFO, Jack, we learn…
-
The New Realities of Vishing: Voice Phishing Hotel and casino giant MGM Resorts reported losses from a recent vishing attack that exceeded 110 million dollars. Vishing involves a convincing phone call, rather than email, to trick targets into divulging sensitive information. With robocalls, telemarketers and full-on cybercriminals all trying to…
-
Workplace Physical Security Is an Essential Component of Cybersecurity While cybersecurity threats sit at the forefront of everyone’s minds, a physical security breach can be every bit as damaging to an organization. In this episode, staring Joey Lawrence as Jeff, we learn about the methods often deployed by bad actors…
-
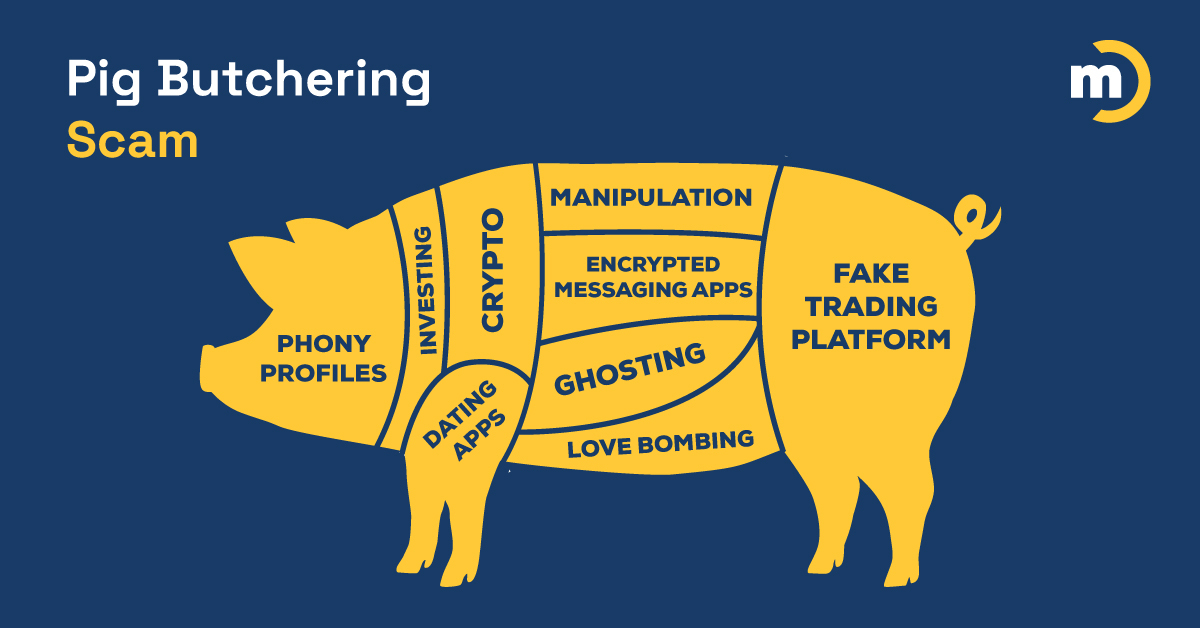
‘Pig butchering’: Former romance scammer reveals tactics. The ‘Pig Butchering Scam’ has become the scourge of the internet. A long con that tricks victims into sending money to fraudulent investment platforms, it has exploded to become the costliest scam out there, with victim losses totaling tens of billions of dollars…
-
Who Do You Think You’re Talking To? A UK-based energy company was recently scammed out of $243,000 by hackers running a “Deep Fake Audio Scam,” a scam that uses artificial intelligence (A.I.) to replicate voices of people we know and trust. In this episode, starring Robert Davi as Louie Sr.,…
-
Zero Trust Cybersecurity: ‘Never Trust, Always Verify’ Grand Theft Auto video game developer, Rockstar, and ride-share giant, Uber, both suffered recent, similar attacks that occurred within a few days of each other. Both incidents could have been avoided by employees adhering to a strict policy of – ‘verify before you…