Imagine this: You get a message. It’s from someone you know well. They urgently need a WhatsApp verification code. Thinking you’re helping, you send it. Big mistake. You just gave a scammer access to their account. This is WhatsApp OTP fraud, and it’s a big problem. It uses our trust…
-
-
New Digital Fraud: Understanding and Protecting Yourself Did you know that digital fraud costs people billions every year? It’s a big problem, and it’s only getting worse. Digital fraud is any type of scam that happens online. From fake emails to bogus websites, crooks are always finding fresh ways to…
-
WhatsApp Fraud: How to Spot Scams and Protect Yourself Have you ever gotten a weird message on WhatsApp from a “friend” asking for money? Sadly, you aren’t alone. WhatsApp fraud is on the rise, and scammers are getting sneakier all the time. Falling for these scams can lead to losing…
-
Deepfake Video Call Scam: How to Spot It and Protect Yourself Imagine getting a video call from your child, their face filled with fear, begging for money because they’re in trouble overseas. It’s a parent’s worst nightmare, right? But what if that call wasn’t real? What if it was a…
-
GIGO: Why Garbage In, Garbage Out Still Matters in the Age of AI Ever tried baking a cake with old, expired ingredients? The result is a disaster. That’s what happens when you use bad data. It’s like the saying goes: Garbage In, Garbage Out (GIGO). This term started way back…
-
Is It Always Good To Update Your System’s OS? IDK. Apple recently urged its users to update their iPhones, iPads and Mac computers after a security flaw allowed hackers to take over these devices. Updating your software in a timely manner is crucial to keeping your devices and information secure.…
-
In the ever-evolving landscape of cybersecurity threats, watering hole attacks have emerged as a sophisticated and insidious method used by cybercriminals to compromise targeted individuals or organizations. As we navigate through 2024, understanding the nuances of these attacks becomes crucial for both individuals and businesses to bolster their defenses effectively.…
-
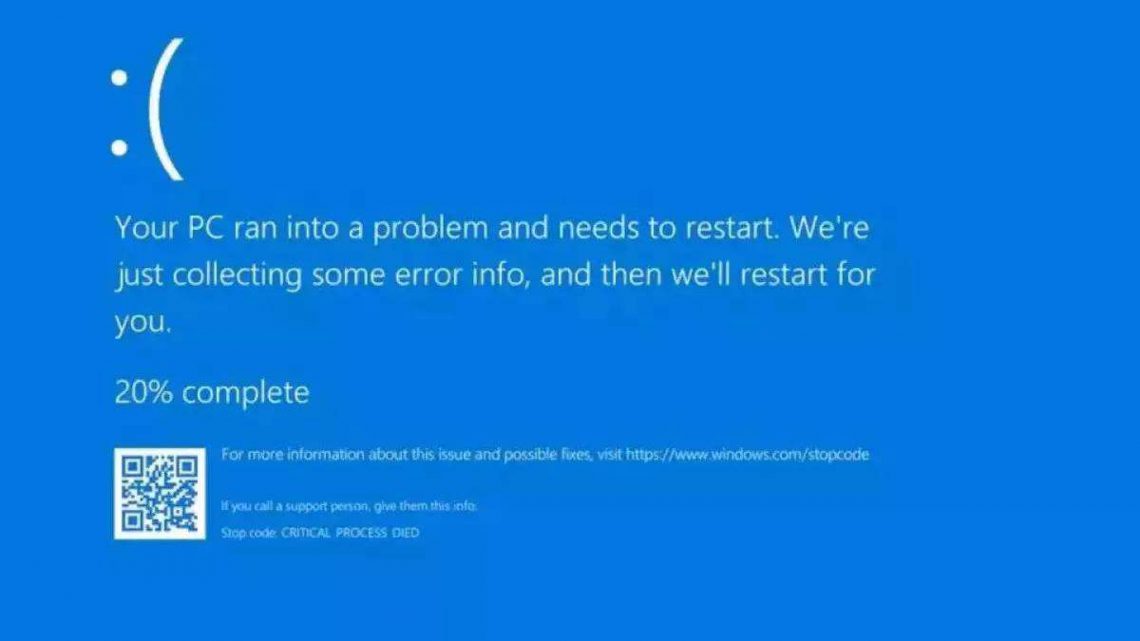
On July 19, 2024, millions of users worldwide experienced disruptions in accessing critical Microsoft services, including Azure, Microsoft 365, and Teams. This widespread outage, attributed to [brief description of the cause, e.g., a technical issue or server outage], underscored the interconnectedness of modern digital infrastructure and the impact of such…
-
In an increasingly digital world where our identities and personal information are stored and accessed online, the security of our credentials—usernames, passwords, and other sensitive data—is paramount. Whether you’re an individual managing personal accounts or an organization safeguarding critical business systems, practicing good credential hygiene is essential to mitigate the…
-
In the realm of digital manipulation and artificial intelligence, deepfakes have emerged as a powerful yet concerning technology. Deepfakes refer to manipulated videos, images, or audio recordings that use advanced AI algorithms to create convincing simulations of real people saying or doing things they never actually did. While deepfake technology…