Is It Always Good To Update Your System’s OS? IDK. Apple recently urged its users to update their iPhones, iPads and Mac computers after a security flaw allowed hackers to take over these devices. Updating your software in a timely manner is crucial to keeping your devices and information secure.…
-
-
As of the latest updates, one significant incident regarding data privacy involved Facebook (now Meta) and the leak of over 530 million users’ data in April 2021. Here’s an overview of this incident. Introduction: Introduce the incident where the personal data of millions of Facebook users was leaked, highlighting its…
-
In an era where technology intertwines deeply with our daily lives, the rise of sophisticated scams poses a significant threat to individuals and businesses alike. From phishing schemes to elaborate Ponzi schemes, the landscape of fraud continues to evolve, making it crucial for everyone to stay informed and vigilant. The…
-
In the ever-evolving landscape of cybersecurity threats, watering hole attacks have emerged as a sophisticated and insidious method used by cybercriminals to compromise targeted individuals or organizations. As we navigate through 2024, understanding the nuances of these attacks becomes crucial for both individuals and businesses to bolster their defenses effectively.…
-
In an increasingly digital world where our identities and personal information are stored and accessed online, the security of our credentials—usernames, passwords, and other sensitive data—is paramount. Whether you’re an individual managing personal accounts or an organization safeguarding critical business systems, practicing good credential hygiene is essential to mitigate the…
-
In the realm of digital manipulation and artificial intelligence, deepfakes have emerged as a powerful yet concerning technology. Deepfakes refer to manipulated videos, images, or audio recordings that use advanced AI algorithms to create convincing simulations of real people saying or doing things they never actually did. While deepfake technology…
-
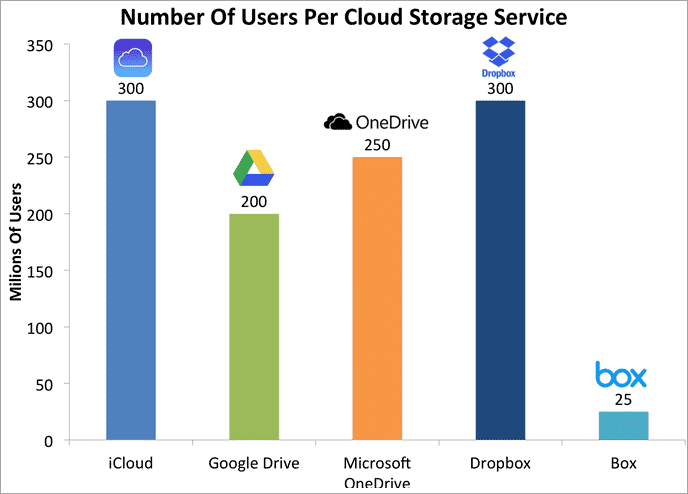
In the era of digital transformation, personal cloud storage has revolutionized the way individuals manage and access their data. From photos and documents to music and videos, the convenience of storing everything in the cloud offers unparalleled accessibility and flexibility. However, this convenience comes with inherent risks that every user…
-
Twilio hack investigation reveals second breach, as the number of affected customers rises. Cybercriminals are becoming more sophisticated in their approach, with Twilio becoming one of more than 130 organizations to fall victim to a large-scale VISHING and SMISHING campaign. The financial as well as emotional damage of such attacks…
-
Social Media Horror Show Twitter and WhatsApp were recently breached, resulting in more than 500 million users having personal data stolen. Social media attacks provide new opportunities for bad actors to target user accounts with increasingly sophisticated attacks. In this episode, starring Robert Davi as our CFO, Jack, we learn…
-
What is clone phishing? Attack of the Clones! News publisher, The Guardian, fell victim to a suspected phishing attack, through which the personal information of UK staff members was stolen. Phishing has evolved to include “clone phishing,” which is highly sophisticated and more difficult to spot. A clone phishing attack…