Messages and Emails are not always friendly
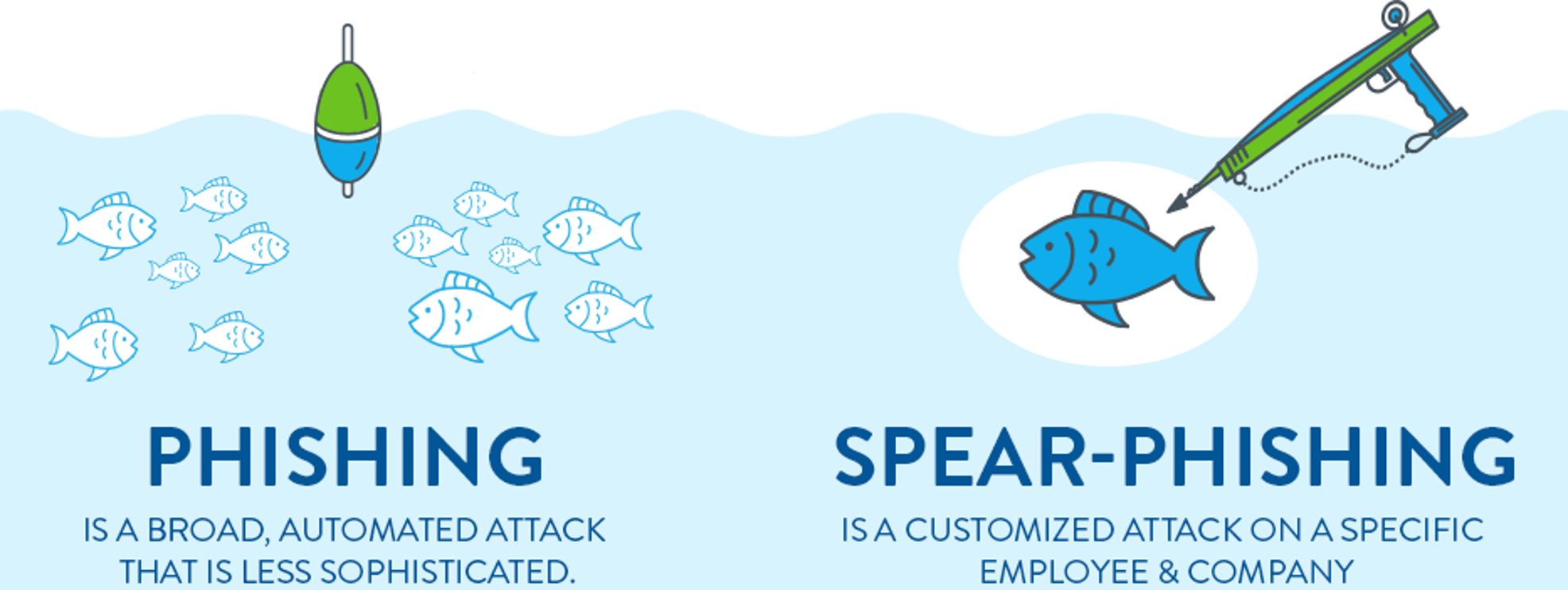
What is Spear Phishing?
Does it go to help me to get a big fish while phishing?
Of course, it will help, but not you because you are going to be that fish 🐠 Let’s know how.
Spear phishing is used to target by using emails to attack by purporting to be from a trusted sender. Spear phishing, as the name implies, involves attempting to catch a specific fish. A spear-phishing email includes information specific to the recipient to convince them to take the action the attacker wants them to take. This starts with the recipient’s name and may include information about their job or personal life that the attackers can glean from various sources.
Spear phishing messages are often crafted with care using pernicious social engineering techniques and are difficult to defend against with mere technical means.
In these attacks, attackers often use information gleaned from research to put the recipient at ease. The ultimate aim is to either infect devices with the malware by convincing the recipient to click a link or download an attachment, or to trick the recipient into taking some other action that will benefit the attacker, usually handing over information or money.
How do spear phishing attacks work?
How attackers get the personal information they need in order to craft a spear-phishing email is a critical spear-phishing technique, as the entire process of the attack depends on the messages being believable to the recipient.
There are several ways an attacker can pull this off. One involves compromising an email or messaging system through other means via ordinary phishing, for instance, or through a vulnerability in the email infrastructure. But that’s just the first step in the process.
Someone’s email within the targeted organization is compromised, and the attacker sits in the network for a while to monitor and track interesting conversations. When the time is right, they email the target using a believable context with insider information, such as bringing up past conversations or referencing specific amounts for a previous money transfer.
How to save yourself from being a fish?
There are some that can help. When it comes to cybersecurity, the same principle of protecting your physical wallet applies to your online activity. You don’t want to become a victim and so we have to explain to everyone why it’s important to do things like turn on two-factor(2FA) or multi-factor(MFA) authentication, use strong passwords that are unique for each account, and utilize a password protection vault to contain online credentials, also a way to use one-time passwords for each login.
the best way to prevent spear phishing is just to keep your suspicious mind engaged. “Phishing scams often come from trusted contacts whose email accounts have been compromised or cloned. Our desire to trust people, to believe that most people are decent, is what is taken advantage of in every phishing attack, and that desire has to be suspended, at least during business hours.”